Everything you need to know about End-of-support in the ever-evolving technology landscape
In an age where technology is deeply intertwined with our daily lives, the importance of timely upgrades cannot be overstated. As we continue to rely more heavily on digital tools for work and leisure, understanding the implications of “end of support” becomes critical.
However, the end of support is not always a bad thing. Often when hardware or software support expires, it is because better, more robust versions are available to enhance your digital experience further.
This End-of-support guide will walk you through everything you need to know about End of Support, when is the best time to upgrade your tools and when can you hold off on the upgrades. Get started here:
- What is End of Support?
- Why should you avoid using unsupported systems?
- How can you minimize risks and protect your organization from technology that is approaching End of Support?
- When is the best time to act for End of Support?
- What are the upcoming End of Life and End of Support to look out for in 2023?
- I’m ready to discuss my End of Life or End of Support Needs with a Konica Minolta Specialist
What is End of Support?
End of support refers to the point in time when a product or software no longer receives official updates, security patches or technical assistance from its Original Equipment Manufacturer (OEM) or Developer. This means that users of the product should be aware that it may become vulnerable to security risks, bugs and compatibility issues if they continue to use it beyond its end-of-support date. It is advisable to upgrade or replace the product to ensure continued reliability and security.
Why should you avoid using unsupported systems?
In today’s ever-changing technology and security threat landscape, it’s critically important to ensure that the operating systems (OS) and applications that your organization is using are supported by the corresponding vendors. Unsupported software presents significant risks to organizations, including security vulnerabilities, compliance issues and productivity concerns. Supported software, on the other hand, receives regular security and functionality updates, third-party application support and usually some level of technical support.
Here are the three specific reasons why you must avoid tools that are approaching or have passed their end of support:
- Security risk: One of the most significant risks of using unsupported systems is related to security. Applications or OS that are out of support won’t receive security updates that address newly discovered vulnerabilities, leaving them open to exploitation by cybercriminals. As time goes on, these exposures increase, potentially impacting other systems within your organization’s network. Hackers can use exploit kits that target these vulnerabilities to compromise networks, steal data or deploy ransomware.
- Compliance risk: Industries that focus on privacy and security often have regulatory requirements that mandate the use of only supported software. From a cyber insurance perspective, supported operating systems, with regular security patching, are often a requirement that can impact the cost of insurance, or in some cases the ability to secure it at all.
- Decline in Productivity and Efficiency: System issues may cause extended downtime as no technical support is available, leading to data loss and negatively affecting operations. Third-party applications installed on unsupported operating systems may become unsupported. Many vendors of these applications only test or release updates for supported operating systems. Over time, these applications will run less effectively – or not at all.
How can you minimize risks and protect your organization from technology that is approaching the End of Support?
When it comes to mitigating risks and safeguarding your organization from technology that is nearing its end of support, there are several strategies you can consider.
Firstly, it’s important to have a good understanding of your inventory. Know which technologies are being utilized within your organization and keep track of their end-of-support dates. This proactive monitoring allows for sufficient time to plan for upgrades or migrations.
Secondly, consider partnering with a third-party support provider. They can fill the gap when the OEM support expires, ensuring uninterrupted coverage and continued remediation of any issues.
Lastly, develop a technology refresh plan. Regularly updating your IT equipment keeps you clear of EOS problems and provides opportunities for performance improvements and feature enhancements.
Remember, the aim is to avoid the vulnerabilities and risks associated with unsupported technology. By staying ahead of the game, you put your organization in the best possible position.
When is the best time to act for End of Support?
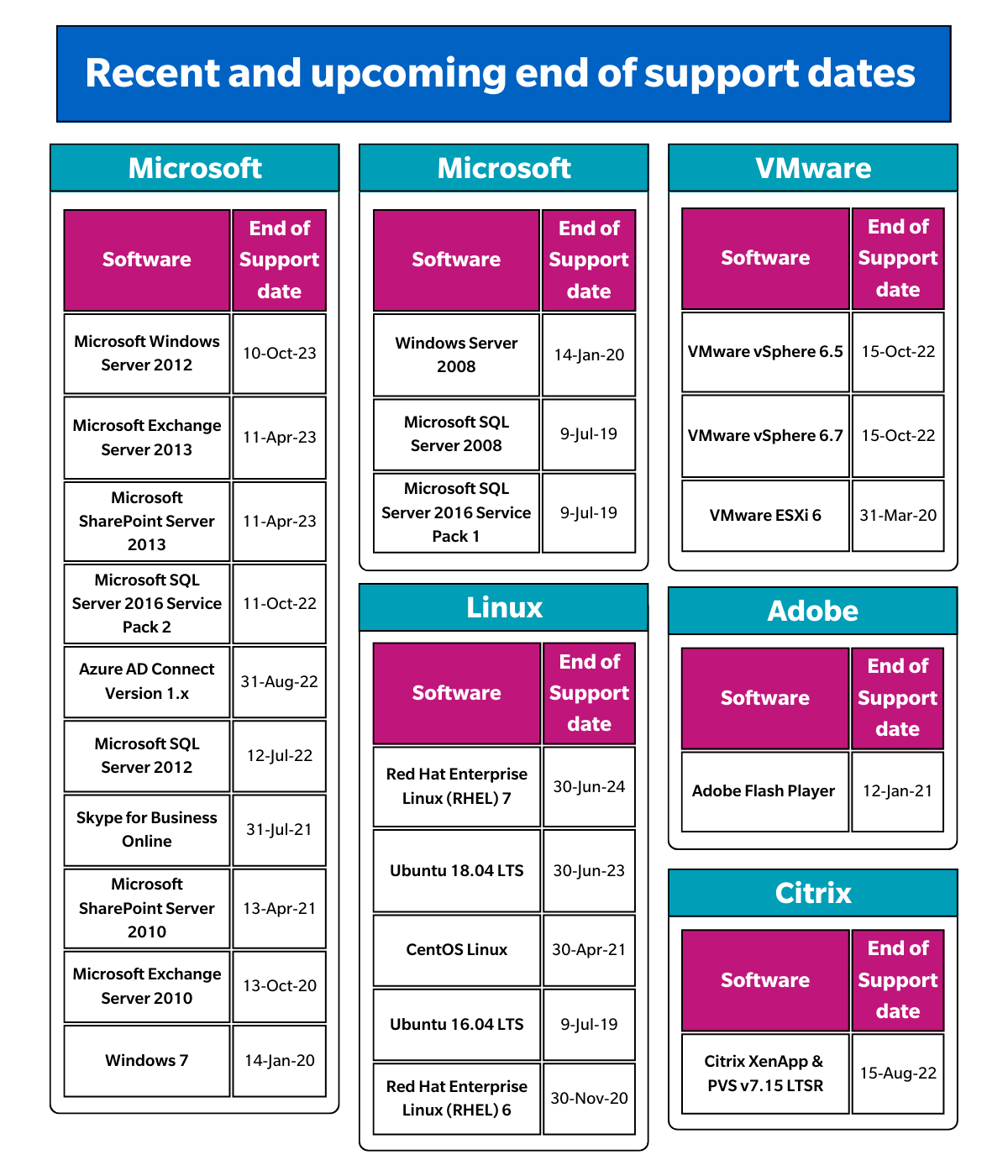
Our security experts recommend starting by having a plan in place to upgrade or migrate systems to supported operating systems or applications. If upgrading is not feasible, consider implementing mitigations such as segmenting networks and applying stricter access controls, utilizing separate passwords for unsupported systems and adding additional security monitoring for these systems. To simplify this process, we have compiled a list of recent and upcoming end-of-support dates for popular supported software. By keeping track of these dates, you can ensure your organization is using the latest supported versions of software and limiting operational impact.
What are the upcoming End of Life and End of Support to look out for in 2023?
Here is a list of tools that have recently reached or will be soon reaching their end of support.
I’m ready to discuss my End-of-life or End-of-support Needs with a Konica Minolta Specialist
If you need help identifying unsupported systems, creating a plan for software support, or implementing any of the recommended mitigations, don’t hesitate to reach out to Konica Minolta’s team of security experts.




